o365 Client SIEM Integration
July 28, 2019Office 365 Security Incident Response
Client currently leverages its on-premises SIEM solution and plans on integrating it with Azure event hub / Office 365 security incident response capabilities to collect security audit logs. These logs are including but not limited to the Activity logs from Exchange Online, SharePoint Online, OneDrive for Business and Azure Active Directory services. SIEM solution will handle the alerts as part of the central monitoring capabilities.
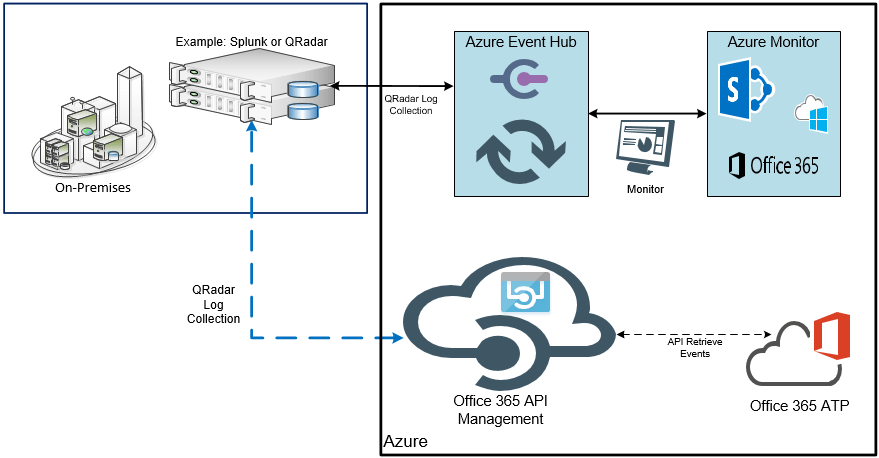
BestITDocuments recommends that Client configure Splunk, QRadar or other enterprise SIEM with a pull relationship with O365 to collect the logs. Client should load their test environment to ensure it is able to support the logs being ingested from O365. Microsoft does not have any tools to help with this, so 3rd party tools and manual testing will be required.
Additionally, Client should ensure they are collecting all the attributes they require in the logs being ingested.
They may need certain services such as O365 Advanced Threat Protection (ATP) to be enabled in order to have all the attributes necessary to meet security threat decisions.
Until Client can integrate or develop a permanent solution. Client should leverage the O365 Service Health dashboard for monitoring and health of the services. Long term, the client can utilize the O365 communications and management APIs which allow the real-time retrieval of service health information and Message Center communications for one or more domains that they own or manage.
By developing a solution using the API’s, or using a 3rd party solution, Client can ensure their requirements are met to monitor service health, manage communications, and develop plans to respond to upcoming service maintenance.
Client should extend its existing Security Incident Response methodology (SIRT) to the Office 365 tenant.